Describe the Steps in the Information System Security Audit Process
Communicate emerging issues potential risks and audit results to your key stakeholders. This is the first step in the audit process flowchart above where we as auditors are appointed to perform the audit work on the clients financial statements.

Pin By Do Thanh On Cobit Itil Change Management Models Management Information Technology Services
Detection risk assessment.

. Perform the audit and gather appropriate evidence. In this phase the system auditor tries to comprehend the management practices and various functions used at multiple levels of the IT hierarchy. Various steps involved in an information systems audit process include obtaining the background information understanding the controls developing the audit plan compliance test of controls use of analytical review procedures summary.
It will also likely include a preliminary list of unresolved issues. Step 2 the planning phase. We develop the audit plan for the subsequent year based on the results of this assessment and the departments available resources.
But before we dig into the varying types of audits lets first discuss who can conduct an audit in the first place. So IS auditors also follow the auditing process that other auditors do. Primarily this is a four stage process.
This document details the purpose of the audit the procedures the auditors used the documents reviewed and the audits findings. A cyber security audit consists of five steps. Summary of Audit Process.
A risk assessment is carried out to develop an audit plan. The Process of Auditing Information Systems - Part 1. Major Steps in the Auditing Process.
Isaca IT audit assurance standards. Perform the auditing work. Manage the audit process in accordance with IS audit standards.
Communicate the results and recommendations to stakeholders. After being appointed as auditors we can start the initial planning of. Raising employee awareness is a great way to transform them from a liability to a useful asset when it comes to cyber security.
Evaluate the operational efficiency of processes. Identify the effects of laws and regulations on IS audit planning. When the auditing team completes the fieldwork and document review the auditors prepare a draft audit report.
Assess your assets. Knowledge of business and industry. Identify best practices in IS audit resource management.
Access controls which prevent unauthorized personnel from entering or accessing a system. Identify best practices for planning audits. CISA REVIEWChapter 1 Risk Based Audit Approach.
Evaluate processes to determine if theyre reliable. A network security audit is a technical assessment of an organizations IT infrastructuretheir operating systems applications and more. Lay out the goals that the auditing team aims to achieve by conducting the IT security audit.
Collection of audit evidence. Information systems security more commonly referred to as INFOSEC refers to the processes and methodologies involved with keeping information confidential available and assuring its integrity. This step determines whether or not the auditor will proceed with the rest of the rest.
Plan audits ensuring the scope matches the needs of the organization being audited. You could say this is the central objective of the audit process but its necessary to list others. Conduct historical due diligence.
The audit plans should define these steps which will be applied by the auditor to obtain audit evidence Audit Evidence Audit evidence is information gathered by auditors during the course of an audit whether internal. Step 1 the selection phase. For more help conducting your own audit check out our mini-guide that explains why you should do an internal security audit and walks you through exactly how to run one for your business in more detail.
Conduct audits in accordance with IS audit standards guidelines and best practices to meet your planned audit objectives. Here are the vital steps of performing a system audit. Selection Phase Internal Audit conducts a University-wide risk assessment near the end of each calendar year.
Your first job as an auditor is to define the scope of your audit by writing down a list of all your assets. Selection Planning Execution Reporting and Follow-Up. This stage may require the auditors to look through relevant business documents and previous audit results.
Advice on the implementation of. Here are details of activities that you will be doing in each step of auditing process. Describe characteristics of the IS audit function.
Recognize the task and knowledge statements of domain 1. Recent financial information. An oft-forgotten step in security audits is pre-audit due diligence.
Establish scope and objectives of the audit. For smaller companies the role of an internal auditor may be. The 4 simple steps mentioned above defining the scope of an audit defining the threats assessing the risks associated with each individual threat as well as assessing existing security controls and devising the new controls.
Verify that the process chain provides protection for company assets. Find out if your company information and data is secure and reliable. Obtain Understanding of Internal Control.
Gather Information and Plan. The Steps in an IT Security Audit. This due diligence should focus on historical events such as known vulnerabilities damage-causing security incidents as well as recent changes to IT infrastructure and business processes.
There are five phases of our audit process. Why how when and who. During the process of the preliminary assessment an auditor is required to identify and ascertain the amount of risk involved and accordingly develop an audit plan.
In this article we will name this the professional auditing process. Prior years audit results.
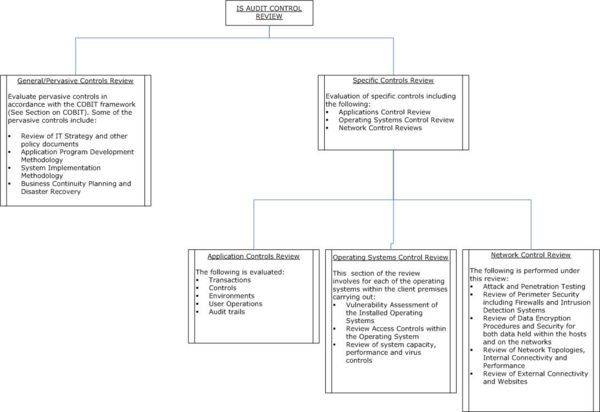
Information Systems Audit Methodology Wikieducator

Isms Process Framework Download Scientific Diagram Framework Process Diagram
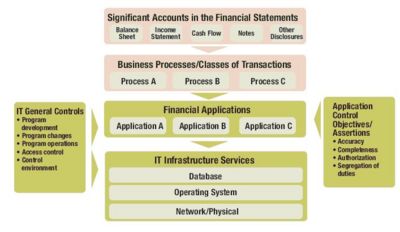
Information Systems Audit Methodology Wikieducator
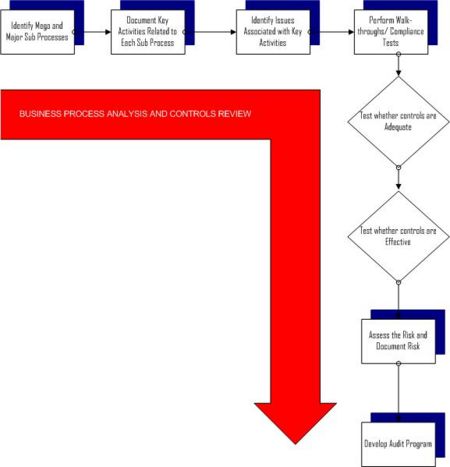
Information Systems Audit Methodology Wikieducator

Iso 27001 Annex A 11 Physical And Environmental Security Infosavvy Security And It Management Training Physics Information Processing Security Tips

Itil Information Security Management Risk Analysis Internal Audit Self Assessment
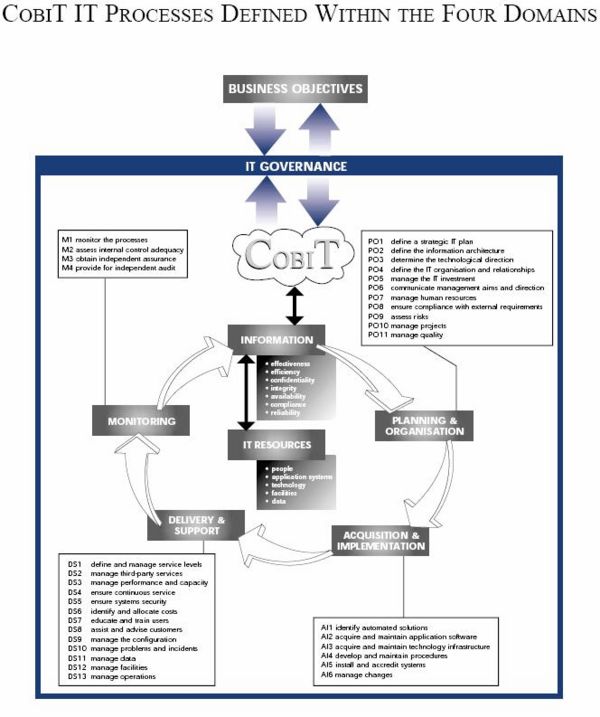
Information Systems Audit Methodology Wikieducator

Cyber Security Tasc Management Cyber Security Security Change Management

10 Steps To Cyber Security Info Savvy Cyber Security Cyber Security Patches

Iso 27001 2013 Information Security Management Isms Hacking Risk Theft Viral Internal Audit Performance Evaluation Risk Management

Cyber Security Program Strategies For Beginners Cyber Security Program Cyber Security Cyber

5 In Demand Cyber Security Certifications Techroots Cyber Security Certifications Cyber Security Data Security

Best Iso Iec 27001 Implementatin Certification Services Certaim Com Risk Management Internal Audit Cyber Security

Iso 27001 Gap Analysis And Iso 27001 Route To Certification Cybersecurity Infographic Cyber Security Awareness Analysis

How To Prepare For Iso 27001 Certification Process Step By Step For Auditee Organizations Iso 13485 Risk Management Risk Management Strategies

How To Perform An Internal Quality Audit Have A Look At This Quality Management Internal Audit Procedure Template And Customize Internal Audit Audit Templates
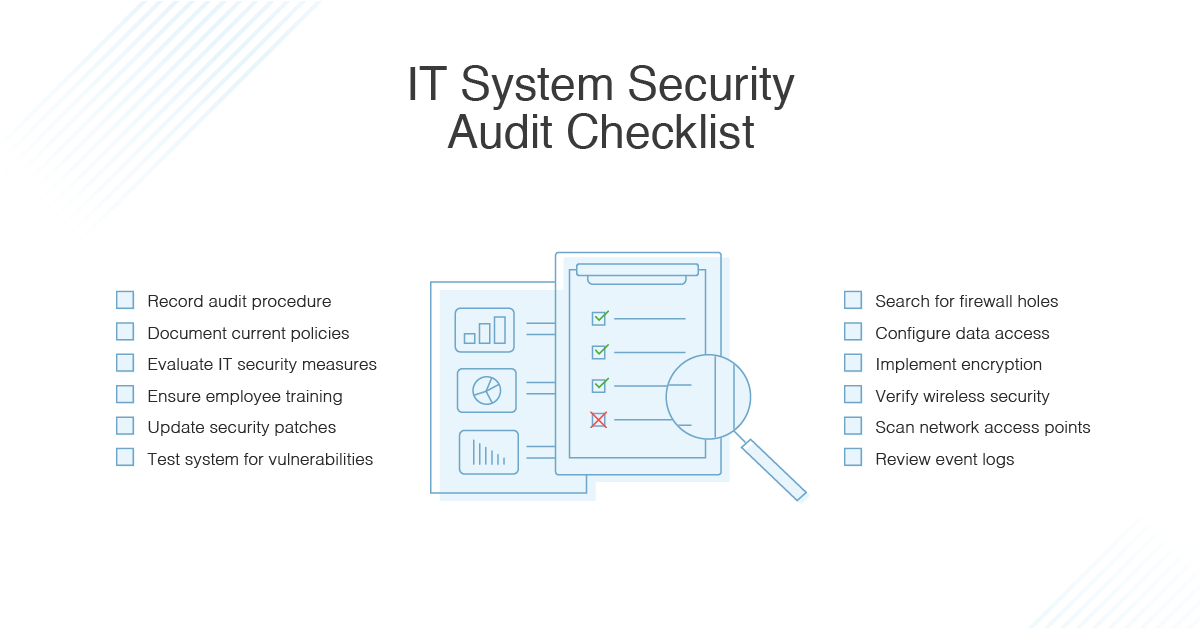
It Security Audit Standards Best Practices And Tools Dnsstuff
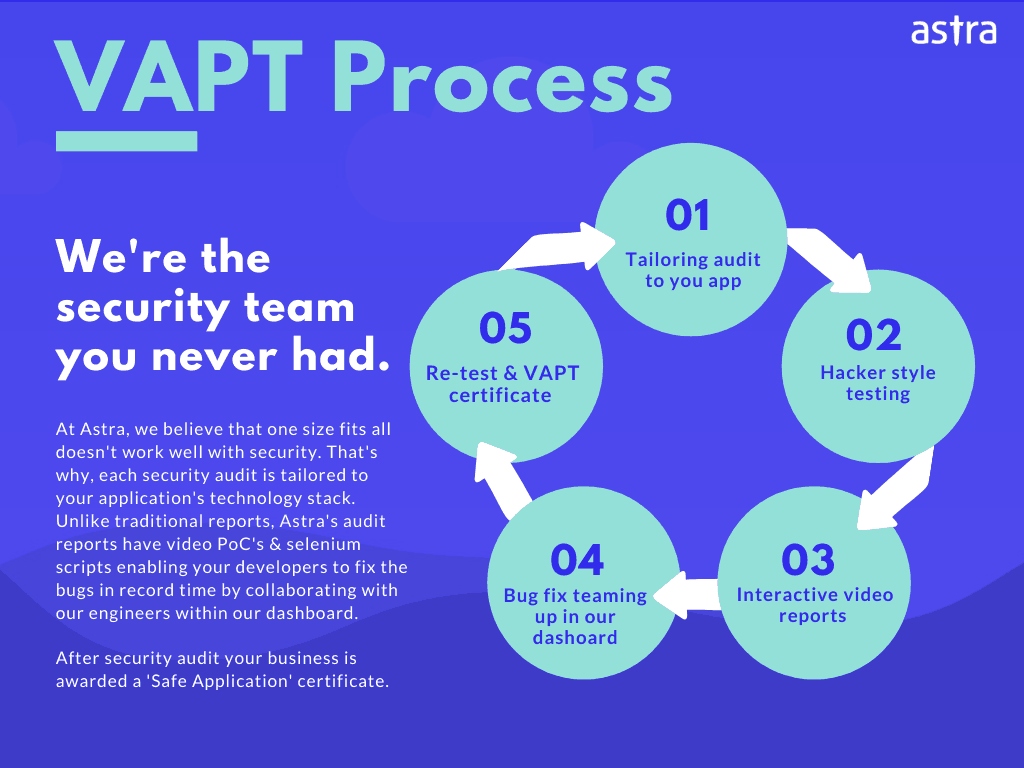
It Security Audit Importance Types And Methodology

Subsystems Of The Accounting Information System Diagram Stock Photo Picture And Royalty Free Image Im Accounting Accounting Information Managerial Accounting

When it comes to safeguarding your network, choosing a reliable partner is crucial. Indian Cyber Security Solutions (ICSS) stands out as a leading NPT service provider in India, offering thorough and expert network penetration testing. Their approach helps identify and address vulnerabilities, ensuring your network remains secure against potential threats. Partnering with ICSS means investing in a secure and resilient network infrastructure.
ReplyDelete